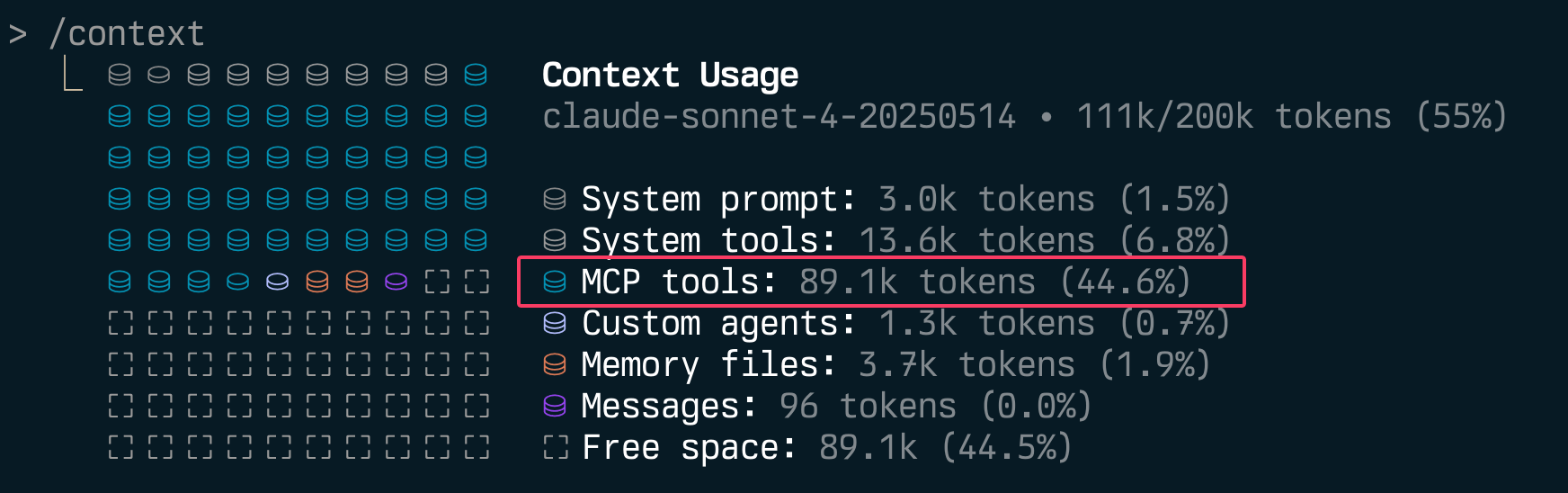
Stop Polluting Context - Let Users Disable Individual MCP Tools
If you’re building MCP servers, you should be adding the ability to disable individual tools.

If you’re building MCP servers, you should be adding the ability to disable individual tools.
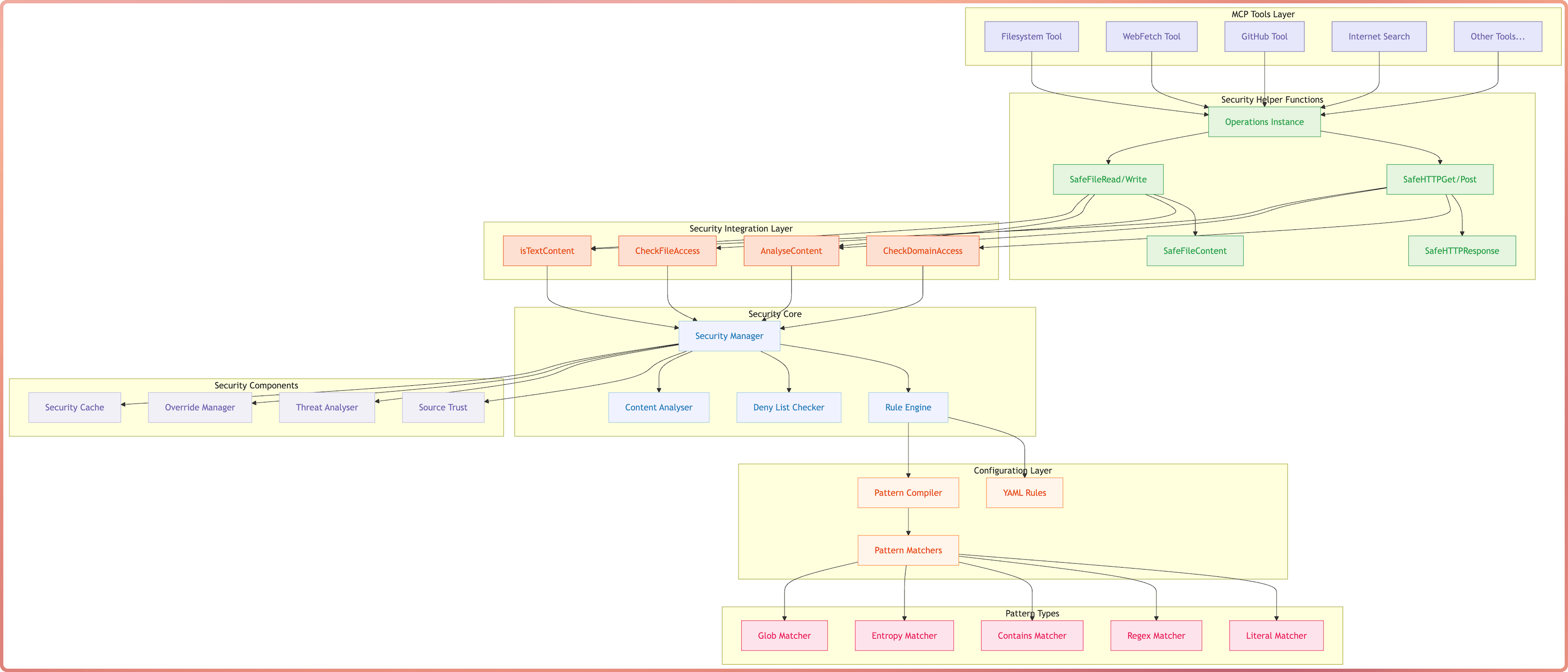
MCP DevTools - The one tool that replaced the 10-15 odd NodeJS/Python/Rust MCP servers I had running at any given to for agentic coding tools with a single server that provides tools I consider useful for agents when coding. The Problem The MCP ecosystem has grown rapidly, but I found myself managing many separate servers, each often running multiple times for every MCP client I had running, not to mention the ever growing memory and CPU consumption of the many NodeJS or Python processes. ...

Inspired by http://zitseng.com/archives/7489 Source (Github) WARNINGS Do not run unless you understand what this is doing The CA system is broken by design - This is not a fix for that This is merely a band-aid for those interested or concerned about these root CAs Usage chmod +x delete_gov_roots.sh ./delete_gov_roots.sh You’ll be prompted for your password as root access is required to delete system-wide root certs. See Also http://convergence.io https://addons.mozilla.org/en-US/firefox/addon/certificate-patrol/ https://github.com/kirei/catt https://www.eff.org/observatory https://bugzilla.mozilla.org/show_bug.cgi?id=478418 http://support.apple.com/en-us/HT202858 https://www.owasp.org/index.php/Certificate_and_Public_Key_Pinning